Digital signature technology is a must-have feature in today’s remote workplace, and there are many solutions on the market to meet the need. However, one product stands out from the rest. Zoho Sign is a flexible digital signature tool that allows you to send, sign, and manage documents from anywhere with a few clicks.
Besides being able to integrate quickly with other Zoho products and a host of third-party applications, Zoho Sign’s greatest claim to fame is its security and data integrity features. Here are five tips to implement to get the most secure experience with Zoho Sign based on some common usage scenarios.
Enable Multi-Factor Authentication
Digital signatures are used to show the authenticity of a document. The reason that so many people trust them is because of the technology that’s behind the signatures.
Public key infrastructure (PKI) cryptography is used to develop digital signatures. PKI is a form of encryption that can only be decoded by a receiver who has the right decryption key. This type of encryption is reliable enough to be used by the government to help secure state secrets. However, using this technology alone is not enough to keep your network and data safe from sabotage.
Today’s Risks
Hackers are increasingly able to breach networks and compromise data through stolen passwords. Keystroke logging or keylogging is a popular tactic that hackers use to get passwords. During this style of attack, a hacker uses logging hardware or software to record the keystrokes of a legitimate user. He or she then uses the captured password to access the targeted company’s network.
Hackers often gain access to passwords by catching unsuspected users off guard with pharming schemes. Pharming happens when a hacker tries to get a user to fill in a password on a phony website that looks like one that he normally uses. The hacker collects the password data from the phony website and uses it to gain access to the real website.
To combat hacking tricks such as these, IT departments have developed a zero-trust security model. In a zero-trust security environment, IT specialists treat every attempt at network access as a potential security breach. No one is a trusted user before he or she successfully passes a set of verification hurdles. Multi-factor authentication (MFA) is the verification hurdle of the moment for IT experts.
While other organizations ask users to create strong passwords with uppercase letters, numbers, and symbols, progressive IT departments set up MFA that requires users to verify their identities in numerous ways.
Enabling MFA
Zoho Sign is commonly used with Zoho Mail to collect signatures on paperwork and sign documents directly from your Zoho Mail inbox. Before installing the Zoho Sign extension and selecting documents from your inbox that need digital signatures, you should enable Zoho’s MFA features.
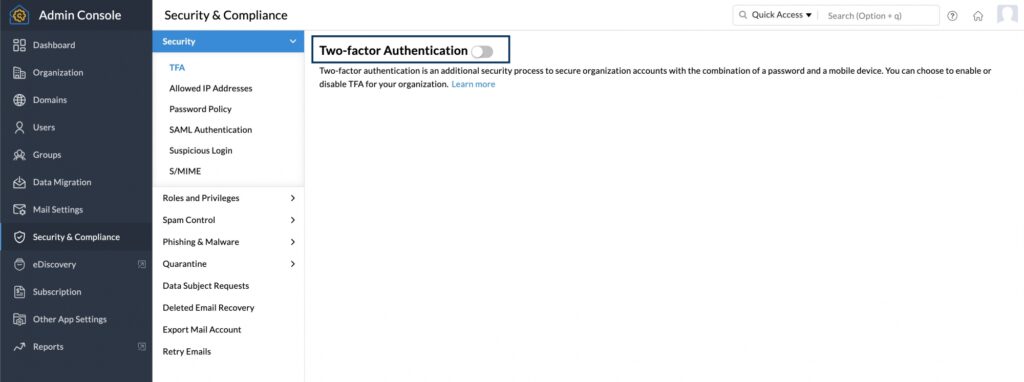
Zoho allows you to choose from among a few MFA mode options. A commonly used one is a time-based one-time password. Time-based one-time password MFAs allow organizations to achieve zero trust security environments by requiring users to verify identities via voice calls or text messages.
Process Documents Within the Zoho Sign Website
Known and unknown internet-facing infrastructure vulnerabilities are key targets for hackers. Once successful, these cybercriminals can capture data at rest, in use, and on the move.
Stealing data at rest is a little easier than hijacking data that are in use or on the move. This data sits on hard drives or in other forms of storage. A firewall makes a great security layer for data at rest.
The next susceptible to attack is data that is in use. These are documents that teams regularly use for collaboration on critical projects. With multiple users accessing the data, there’s more potential for a breach.
Zoho Sign secures data in storage, in use, and on the move. When creating a document within Zoho Sign, it’s automatically converted into a PDF and assigned a cryptographic hash. As a result, Zoho Sign only stores encrypted data on its servers built by Zoho.

Data that’s in use benefits from public-key cryptography for digital signatures. After getting signatures, users can store the signed document on Zoho using 256-bit encryption technology or transmit it to another user for review. Transmitting data within Zoho Sign is always as secure as possible with Secure Sockets Layer / Transport Layer Security protocols in place.
To take full advantage of these security features, process documents within the Zoho Sign website or application when possible.
Use Advanced Endpoint Security
While Zoho offers some of the most secure business tools around, many security vulnerabilities are outside of its control. One source of these vulnerabilities is known to the IT world as network endpoints. Endpoints are devices or nodes that facilitate communication between a user and a network. It’s at these endpoints that hackers launch their most successful attacks.
A common Zoho integration happens when users want to populate contracts with Zoho CRM data. After installing the Zoho Sign extension within Zoho CRM, you can create a contract for a business client, populate the fields with specific customer data, and send the contract out for signature. When the document and its associated data are used outside of Zoho Sign, they are vulnerable to theft or sabotage. However, Zoho keeps everything secure within its own ecosystem of data servers.
Hackers get to this data by launching malware attacks that can’t be detected by traditional antivirus software. Conventional antivirus software relies on threat signatures to identify malware and block suspicious files. Hacking is a lucrative crime in many cases, and cybercriminals don’t hold back when pulling off heists.
Sophisticated hackers modify malware code on the go to penetrate a company’s network security. By the time that your antivirus tool provider updates its threat signatures, the hacker has come and gone with your data. The problem is so pervasive that Symantec’s senior vice president, Brian Dye, conceded that antivirus is dead.
Of course, he meant that old-school, reactive-style antivirus software is dead. Today, advanced endpoint security uses machine learning to proactively identify threats based on user behavior and endpoint activity.
Back Up Documents
Accidents happen. When they involve losing signed, legally binding contracts, your company’s reputation is at stake. If your organization can’t be trusted to hold on to signed contracts in this age of multiple data storage options, can it be trusted to fulfill the contract in a professional manner? That’s what your clients will be discussing back at their offices.
Zoho encourages users to monitor their Zoho Sign documents to make sure that contracts haven’t been lost or accidentally deleted by employees. When an employee accidentally deletes a file, he or she often panics. Smart organizations have plans in place to handle security incidents that involve lost data. Besides executing a comprehensive data recovery response, companies should make data backup a routine part of doing business.
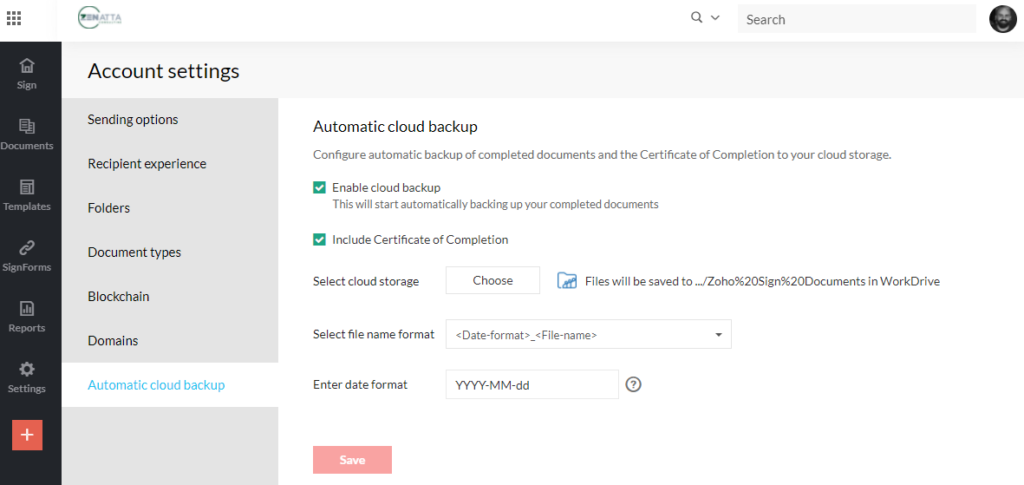
Depending on your company’s requirements, you’ll want to turn on and set up automatic backup to the cloud storage of your choice. Many companies outsource data backup and recovery services to guarantee that extra layer of protection.
Shore Up Identity Access Management
It’s not uncommon for disgruntled employees to launch sneak attacks on their employers out of spite. Need a copy of a signed contract before a big meeting? An irate insider could technically delete signed documents just to “stick it to the man.”
It’s also possible for hackers to penetrate a network undetected and remain there to cause a host of harm. Once they breach the perimeter, they create legitimate user credentials. In essence, they make themselves at home behind your company’s multiple layers of security.
Zoho has IT security in its DNA. Configure most of these at the user level. Rules regarding access permissions and identity management must be in place to ensure that only the right people have access to certain tools, documents, and network spaces.
Conclusion on Zoho Sign Security
According to cybersecurity experts at Security Magazine, attacks that exploit internet-facing infrastructure vulnerabilities are one of the top five cybersecurity threats to watch in 2021. With more companies using cloud services, it’s surprising how many are vulnerable. While it’s true that hackers have become more sophisticated in recent years, you don’t need to slow your company’s progress towards its digital transformation goals. The Zoho tool suite uses military-grade encryption technology to protect important document data during transit, in use, and at rest. Zoho Sign’s built-in security features make it a best-value option among a long list of worthy competitors.
Have you recently integrated Zoho Sign with another Zoho tool or third party app? Tell us about your experience in the comments below.